Data Link Layer
MTU – Usually a suspect with performance or sometimes reachability issues. The tracepath command from iputils can be helpful here.

Data Link Layer
MTU – Usually a suspect with performance or sometimes reachability issues. The tracepath command from iputils can be helpful here.

AWS Direct Connect becomes appealing when you need more than a best-effort assurance of reachability to one or more AWS regions.
Many people think of Direct Connect as more of a privacy construct or something you use when you move to a colocation facility. But really, it’s not – both from an exam and practical perspective. Direct Connect gives you a few different capabilities:
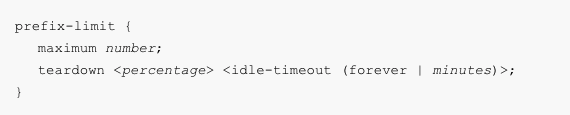
After understanding the networking fundamentals, you need to understand the AWS constructs that are between your organization and your VPC(s).
You have web services and an EC2 database server running in your VPC. You want IPv6 anccrm for both layers. Your VPC has one private subnet 10.0.1.0/24 and hosts the DB instance. This subnet will require only outbound IPv6 and currently has outbound IPv4 using a NAT GW. What should you add to this subnet for IPv6?
What is the best way to make two EC2 instances in private subnets that are the back-end of an internet-facing load balancer reachable?
[missing]
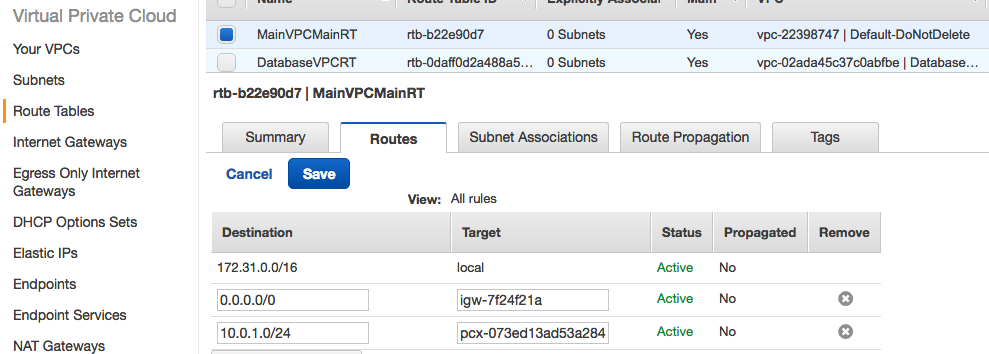
Your VPC route table has two routes to 10.1.1.0/24. One has a propagated VGW target, and one has a manually added IGW target. Which will be preferred?
What are three types of subnets in an AWS VPC?
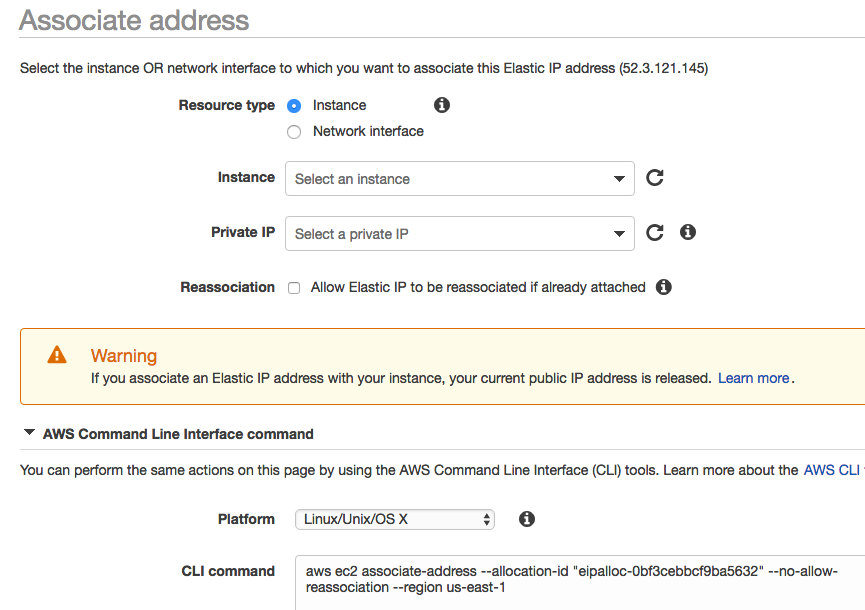
What limits and special conditions apply to Elastic IP addresses?
A customer has an S3 bucket in US-East-1 and a VPC with EC2 instances on private subnet 10.75.85.0/24. EC2 instances need to be able to access S3 bucket without traversing internet. The customer would like to use the most cost effective solution possible. Options?
You use a NAT GW for your EC2 fleet to send content to and from your S3 bucket. Data transfer costs are getting expensive. How can you reduce costs?
Transitive routing: If A is peered to B, and A is peered to C, there is nothing you can add to C’s route table to reach subnets in B.
You have a Postgres cluster in AWS using private IP addresses using a security group to control access to all nodes in the cluster. How can you ensure disaster recovery for these nodes in another region SECURELY?
Company has a Direct Connect endpoint in US-West to on-premise infrastructure using a direct connect partner. Currently this endpoint has 9 VIFs You would like to add more. What are your next steps?
Company has a Direct Connect in US-East-1 (10.1.0.0/16) to their data center but also wants to use it to connect to US-East-2 (10.2.0.0/16). After updating BGP, traffic from East-1 is not reaching East-2. Both VPCs can still access the corporate network. What might be the cause?
What is the limit on the number of propagated BGP routes in a VPC route table?
How many Direct Connect (DX) endpoints do you need to access all US regions over direct connect?
You have 3 VPCs, 10 S3 endpoints and 10 EC2 instances in each VPC. What is the minimum number of Virtual Interfaces for all of your resources to have access to the Direct Connect(ion)?
What are the minimum requirements for your network device to support Direct Connect?
You are using two Direct Connect circuits in a Primary/Backup pattern, but you are finding it takes too long for your Backup to take over when the Primary connection becomes sick but not dead. The same solution should apply if you are using VPN as backup. What will make failover faster?
You need to aggregate and scale Direct Connects to achieve more data throughput to AWS. You decide to use a LAG group. What rules apply?
You have a large amount of on-premise traffic going to S3 that needs to be low, consistent latency and encrypted. What solution will help?
You are setting up a VPN connection between your VPC and on-premise infrastructure. You need to ensure the firewall rules allow this on premise. What ports do you need to allow?
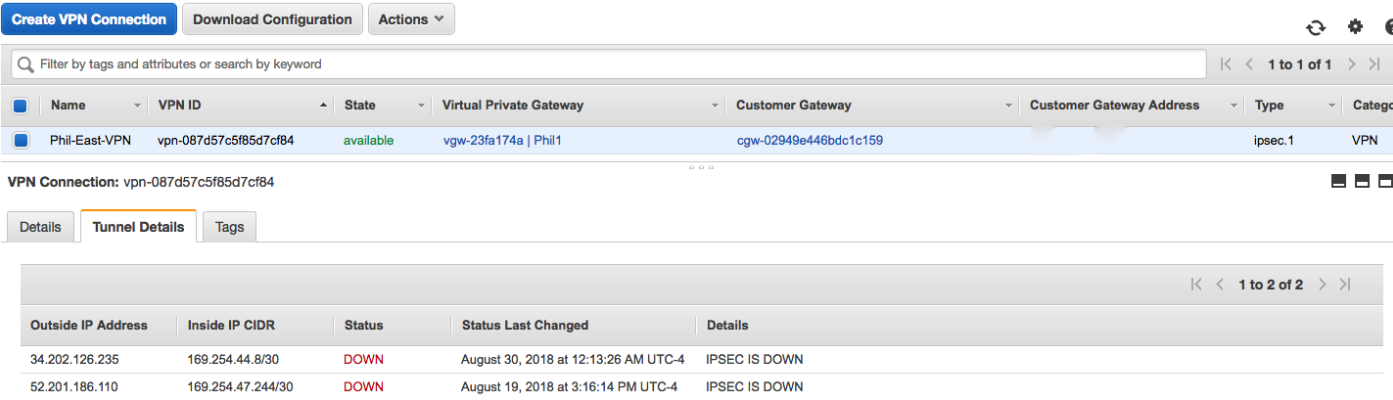
You are setting up a VPC Managed VPN. IKE Phase 1 is established but IPSec Phase 2 is failing. You have the correct IKE version, customer gateway and encryption method. What else might the problem be?
From an AWS perspective, what VPC architecture is recommended for a highly available, low-cost VPN connection to your VPC?
IPSec VPNs are also supported on EC2 instances. Why might the AWS Managed IPSec VPN be more resilient?
Your AWS Managed IPSec VPN to on-premise customer gateway is configured, but when you check the console tunnel status it still shows down. What will bring it up?
You require a GRE VPN between your AWS VPC and a remote site. How?
You have an AWS Direct Connect in US-East-1 and are using a public VIF to access an S3 bucket in the region. You want to use the same Direct Connect to access a S3 bucket in US-West-2 for safekeeping. How can this be achieved at the lowest cost?
You have a Direct Connect in US-East-1 and want to use it to access a VPC in another region? What are two ways to achieve this?
You have just provisioned an Application Load Balancer to distribute your web traffic to a cluster of EC2 instances in the same subnet of a VPC. When you test the web site you receive HTTP 504: Gateway Timeout. What are likely causes of this error?
Company wants to send mobile web traffic (url is /mobile) to memory optimized instances and api calls (url is /wapi) to their largest compute instances. What can enable this?
You are using a Classic Load Balancer for both http:// and https:// connections, but you want your back-end logs to show the client IP, not the load balancer IP.
You have an online commerce application running on EC2 instances (autoscaling and multi-AZ) behind Application Load Balancer service. The application tier must read and write data to customer managed (not RDS) database cluster. You want to ensure no access to these databases from the internet, but you do need to retrieve database patches over internet. What meets this need?
You want to access your RDS DB using your private domain name mydb.acme.org instead of the AWS-provided name. What will enable this?
For both performance and reduced cost, what is a good pattern to use to allow all of your VPCs to access your on-premise DNS servers?
You have a private hosted zone in AWS but want to sure on-premise resources can lookup resources in the AWS zone. Which approach is least effort:
Your EC2 web instance has both a Security Group (allow inbound on port 80 from 0.0.0.0/0, deny outgoing traffic) and NACL (same rules as SG). Users cannot access the web site. What needs to change?
You are unable to ping an instance in another subnet in your VPC. Flow logs show your inbound ping as ACCEPT OK followed by REJECT OK. What is the likely fix?
[Jumbo frames] A peer manager suggested using jumbo frames to improve performance on a VPN connection between your data center and VPC. In what situations can jumbo frames help?
Your EC2 instance will be processing a large inbound traffic flow, and you want to ensure maximum performance for network packet processing. Two suggestions?
You need optimal network performance between EC2 instances in different regions with peered VPCs. What tools do you have?
Application teams who do not manage Direct Connect (or VPN) want to be alerted when the connection to the headquarters office is down. How can they do this?
You want to be alerted any time resources are created. Which 3 services are most helfpul for this?
You have a Lambda function that looks for EC2 events and sends requests to SQS. How is this built?
Your EC2 instance will be a custom origin for a Cloudfront web distribution, but you want to ensure traffic is encrypted in transit. What is required?
A department has set up their own AWS account that is not part of consolidated billing used by the rest of the company. They have a Direct Connect to their VPC using a private VIF. When downloading data from an EC2 instance in the VPC, how could the charges comes across?

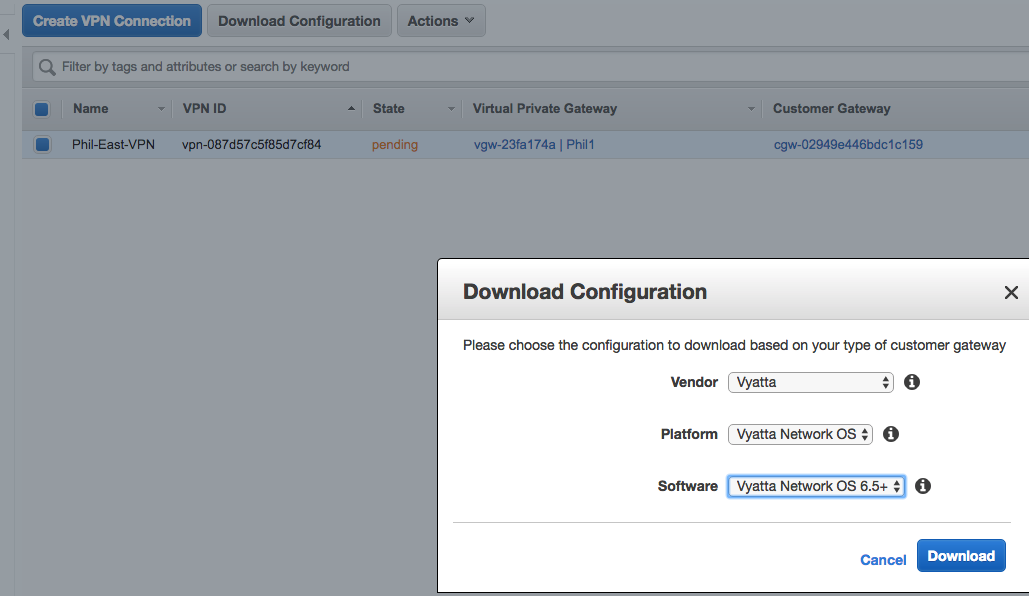
Setting up the VPN
2. Create a Customer Gateway (basically provide AWS with the device type and public IP address of your on-premise VPN termination).
3. Create a VPN connection which binds your VGW and CGW.
4. Download and Apply the VPN configuration file for your on-premise device.
5. Generate traffic from your on-premise network to AWS to initiate the VPN connection. The Customer Gateway must initiate the VPN connection, and with many appliances it requires either keepalive traffic or traffic destined to the VPC (“interesting traffic”)
The fundamental topics in this section underpin most of your communication options in AWS. They are essential building blocks for how your servers communicate, how you route traffic between environments, and how you uncover why your traffic reaching its destination.

| Inbound Rules | ||||
| Protocol Type | Protocol | Port Range | Source | Comments |
| All traffic | All | All | sg-1a2b3c4d | Enables instances in same security group to communicate w/each other. |
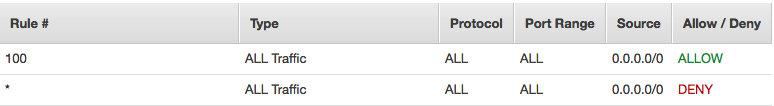
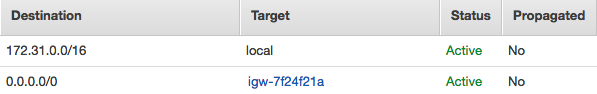
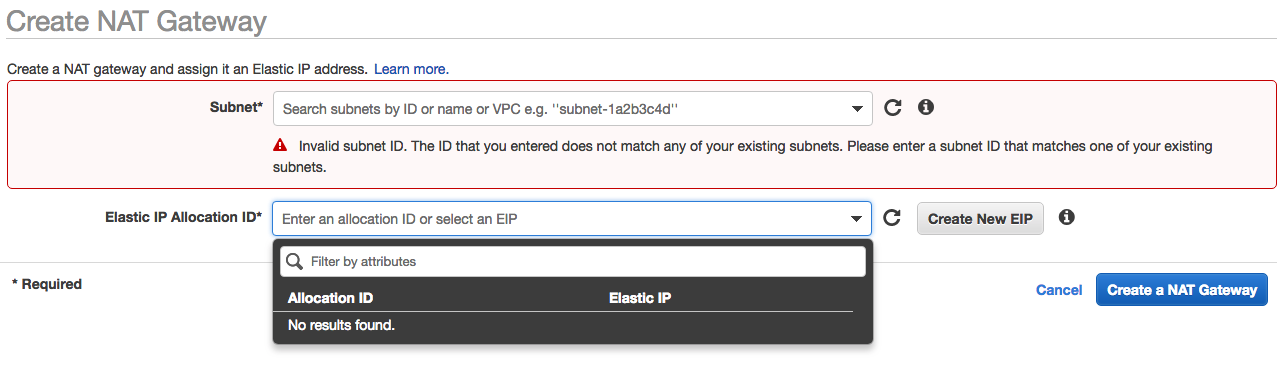

The features below primarily assist EC2 connectivity and performance:
Continue
[Back to AWS Networks Home]
VPC uses a mapping service which abstracts all of your VPC resource information from the underlying infrastructure. Because of this it is likely there is additional header overhead (VPC header, likely q in q) for all traffic in and out of your VPC.
This abstraction is why broadcast and multicast traffic are not supported. There are tutorials on methods to use when your application requires broadcast, but the general exam answer is likely to be rearchitect your application to not require these protocols.
Pay attention to where services reside.
What makes up “AWS Networking?”
Many of the exam questions in this section should be very similar to those from the Solution Architect exam – mostly understanding what services do.
Knowing your management plane risk is important.
[Back to AWS Networks Home]